雷電MAILD 防火牆是一個簡易型的防火牆, 利用系統的 Windows IP Filter Driver 所開發的防火牆功能. 設定介面位於 [伺服器設定]->[基本設定]->[選項]->[IP限制]->[IP/Domain 拒絕清單]->[設定防火牆].
其畫面如下:
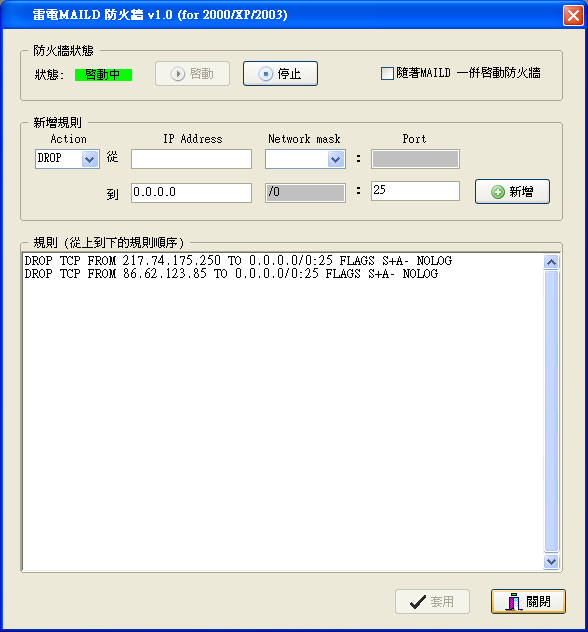
Action
DROP 為丟棄封包(拒絕連線), PASS 為通過封包(接受連線).
來源 IP
IP Address:
設定對方的 IP address.
Network mark:
空白為單一IP.
/24 為 C 網段,
/16 為 B 網段,
/8 為 A 網段.
Port:
(不用設定)
目的 IP
IP Address:
設定本機端的 IP address. 通常為 0.0.0.0 即可, 不然也可為本機端的某個單一IP.
Network mark:
(不用設定)
Port:
本機端要過濾的埠號. 可以用 - (減號) 來表示埠號範圍, 如 1-1024 為 1 到 1024 的埠號都要過濾.
加好規則後, 要先套用存檔後, 再啟動防火牆方可套用新規則.
以上是針對MAILD 會用到的部份才設計的介面, 基本上它可設的規則還有很多, 請參考下列原出處英文的規則說明.
=======================================================
# ----------------------------------------------------------------------------
# IP Firewall Lite Rules Examples
# Rules format: Rules are applied from TOP to BOTTOM! All reserved words must be in uppercase!
# WARNING : THIS IS A SAMPLE AND MUST NOT BE APPLIED TO FIREWALL BECAUSE
# IT MAY NEGATIVELY AFFECT NETWORK PEFORMANCE AND SECURITY!
# ----------------------------------------------------------------------------
#
#
# IP rules:
#
# PASS|DROP IP FROM <addr> TO <addr> [IPPROTO <ipproto>] [NOLOG]
#
#
# Where <addr> is IP-address and possibly netmask (192.168.0.0/24) or "ANY"
# <addr> ::== ANY
# is equal to 0.0.0.0/0
#
# And <ipproto> is IP-protocol number. See etc\protocol file.
#
#
# Example:
#
# PASS IP FROM ANY TO 192.168.0.0/24 IPPROTO 1 NOLOG
# DROP IP FROM ANY TO 127.0.0.1
#
# ----------------------------------------------------------------------------
#
# TCP rules:
#
# PASS|DROP TCP FROM <addr> TO <addr> [FLAGS <flags>] [NOLOG]
#
# Where <addr> is IP-address and possibly netmask or port range
# <addr> ::== <ip_address>[/<mask>][:<port>[-<port2>]]or
# for example 192.168.0.1:1-1023 , 192.168.0.0/24 or
#
# And where <flags> is sequence of one or some TCP-flags: A P S R F U E C
# and '+' or '-' character after (flag is set or flag is not set)
# Be carefull while using flags...If stateful inspection is activated,
# you must be very careful to (albeit not suggested) use them.
#
# Example (deny incoming connections to privileged ports from some subnet):
#
# DROP TCP FROM 192.168.5.0/24 TO 0.0.0.0/0:1-1024 FLAGS S+A-
#
# ----------------------------------------------------------------------------
#
# UDP rules:
#
# PASS|DROP UDP FROM <addr> TO <addr> [NOLOG]
#
# Where <addr> is similiar to TCP rules case.
#
# Example:
#
# PASS UDP FROM ANY TO 0.0.0.0/0:53
# PASS UDP FROM 0.0.0.0/0:53 TO ANY
# ----------------------------------------------------------------------------
#
# ICMP rules:
#
# PASS|DROP ICMP FROM <addr> TO <addr> [TYPE <type>[.<code>] [NOLOG]
#
# Where <addr> is similiar for TCP rules case.
#
# And <type> and <code> is ICMP types and codes.
# For example echo request is 8.0 and echo reply is 0.0.
#
# Example:
#
# PASS ICMP FROM ANY TO 192.168.0.1/32 TYPE 8.0
#
# ----------------------------------------------------------------------------
=======================================================
感謝您看完此篇文章
回知識庫首頁
