RaidenMAILD firewall is a lite firewall designed for blocking hostile IP address. It's technology is based on Windows IP Filter Driver. The configuration is in [Server settings]->[Basic]->[Options]->[IP Restriction]->[IP/Domain Deny List]->[Configure Firewall].
The configuration screen is below:
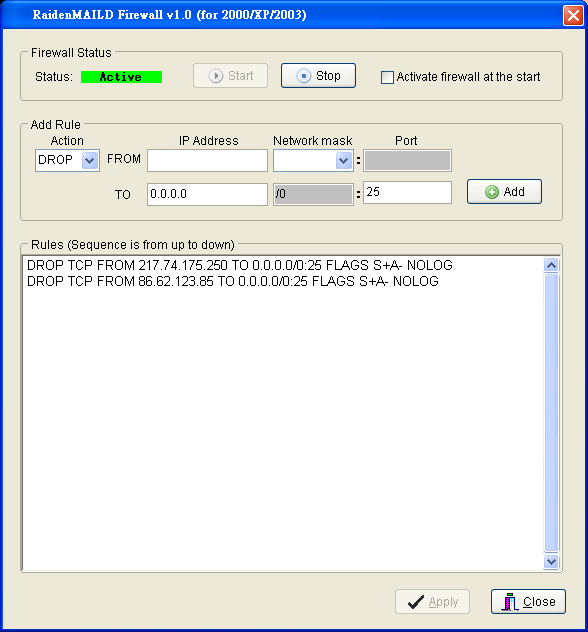
Action
DROP means deny a connection. PASS means allow a connection.
From IP Address
IP Address:
It means remote host IP address.
Network mask:
Empty means single IP address.
/24 means class C of IP address.
/16 means class B of IP address.
/8 means class A of IP address.
Port:
(no necessary to specifiy this)
Destination IP Address
IP Address:
It means local host IP address. Most of case is 0.0.0.0/0 (ANY), or you can specify a single IP address on local machine.
Network mask:
(no necessary to specifiy this)
Port:
The port on local to be filtered. You can specify port range by dash sign ( "-" ), ex: 1-1024 means port from 1 to 1024.
The GUI is only designed for raidenmaild to block IP address. However, this firewall can do more than this. You can refer the original rules document below.
=======================================================
# ----------------------------------------------------------------------------
# IP Firewall Lite Rules Examples
# Rules format: Rules are applied from TOP to BOTTOM! All reserved words must be in uppercase!
# WARNING : THIS IS A SAMPLE AND MUST NOT BE APPLIED TO FIREWALL BECAUSE
# IT MAY NEGATIVELY AFFECT NETWORK PEFORMANCE AND SECURITY!
# ----------------------------------------------------------------------------
#
#
# IP rules:
#
# PASS|DROP IP FROM <addr> TO <addr> [IPPROTO <ipproto>] [NOLOG]
#
#
# Where <addr> is IP-address and possibly netmask (192.168.0.0/24) or "ANY"
# <addr> ::== ANY
# is equal to 0.0.0.0/0
#
# And <ipproto> is IP-protocol number. See etc\protocol file.
#
#
# Example:
#
# PASS IP FROM ANY TO 192.168.0.0/24 IPPROTO 1 NOLOG
# DROP IP FROM ANY TO 127.0.0.1
#
# ----------------------------------------------------------------------------
#
# TCP rules:
#
# PASS|DROP TCP FROM <addr> TO <addr> [FLAGS <flags>] [NOLOG]
#
# Where <addr> is IP-address and possibly netmask or port range
# <addr> ::== <ip_address>[/<mask>][:<port>[-<port2>]]or
# for example 192.168.0.1:1-1023 , 192.168.0.0/24 or
#
# And where <flags> is sequence of one or some TCP-flags: A P S R F U E C
# and '+' or '-' character after (flag is set or flag is not set)
# Be carefull while using flags...If stateful inspection is activated,
# you must be very careful to (albeit not suggested) use them.
#
# Example (deny incoming connections to privileged ports from some subnet):
#
# DROP TCP FROM 192.168.5.0/24 TO 0.0.0.0/0:1-1024 FLAGS S+A-
#
# ----------------------------------------------------------------------------
#
# UDP rules:
#
# PASS|DROP UDP FROM <addr> TO <addr> [NOLOG]
#
# Where <addr> is similiar to TCP rules case.
#
# Example:
#
# PASS UDP FROM ANY TO 0.0.0.0/0:53
# PASS UDP FROM 0.0.0.0/0:53 TO ANY
# ----------------------------------------------------------------------------
#
# ICMP rules:
#
# PASS|DROP ICMP FROM <addr> TO <addr> [TYPE <type>[.<code>] [NOLOG]
#
# Where <addr> is similiar for TCP rules case.
#
# And <type> and <code> is ICMP types and codes.
# For example echo request is 8.0 and echo reply is 0.0.
#
# Example:
#
# PASS ICMP FROM ANY TO 192.168.0.1/32 TYPE 8.0
#
# ----------------------------------------------------------------------------
=======================================================
Thanks for your reading.
Back to Index
Last update : 2007/10/21 |
